SOC170 – Passwd Found in Requested URL – Possible LFI Attack
By: Tanner Adler
Introduction
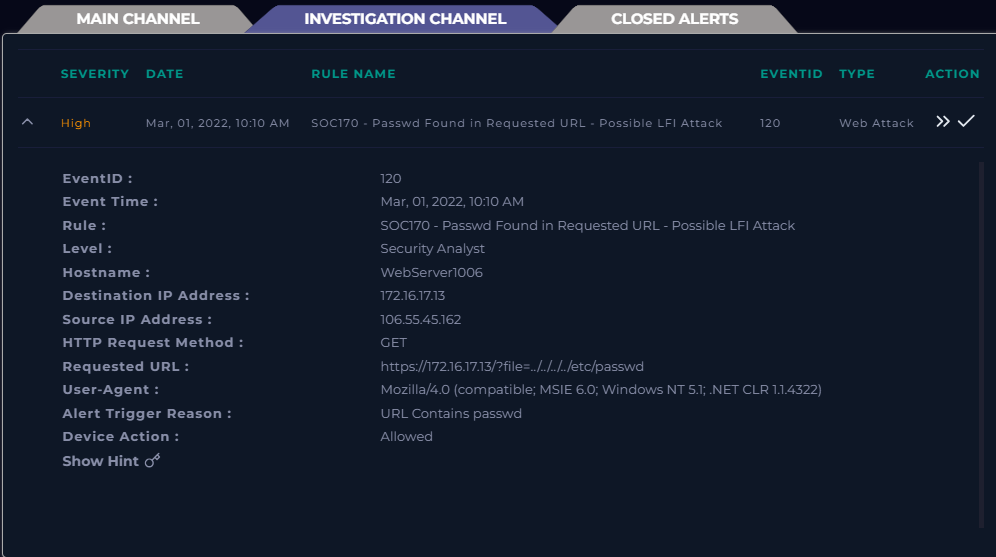
This post walks through my investigation of a “High” severity alert in the LetsDefend SOC platform. The case centers around EventID: 120 (Rule: SOC170 – Passwd Found in Requested URL – Possible LFI Attack), which at first glance appears suspicious since the requested URL contains directory traversal into the /etc/passwd/ file on a Web Server.
Alert Overview
The alert triggered on March 01, 2022, at 10:10 AM, when the SIEM detected the string passwd in a requested URL
https://172.16.17.13/?file=../../../../etc/passwd
This path is a classic indicator of a Local File Inclusion (LFI) attack, where an attacker attempts to access sensitive files by manipulating input parameters.
-
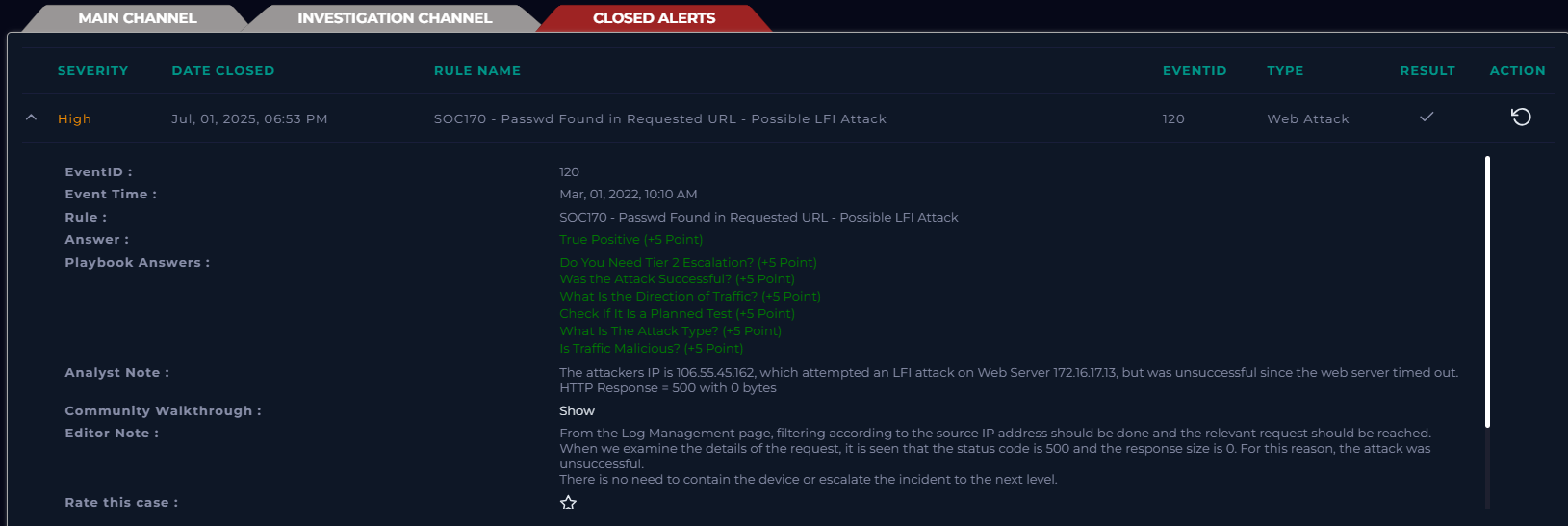
EventID: 120
-
Rule: SOC170 – Passwd Found in Requested URL – Possible LFI Attack
-
Level: Security Analyst
-
Hostname: WebServer1006
-
Destination IP Address: 172.16.17.13 (letsdefend.io)
-
Source IP Address: 106.55.45.162 (Internet)
-
Request Method: GET
-
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; .NET CLR 1.1.4322)
Event & Endpoint Details
Raw Log Evidence
-
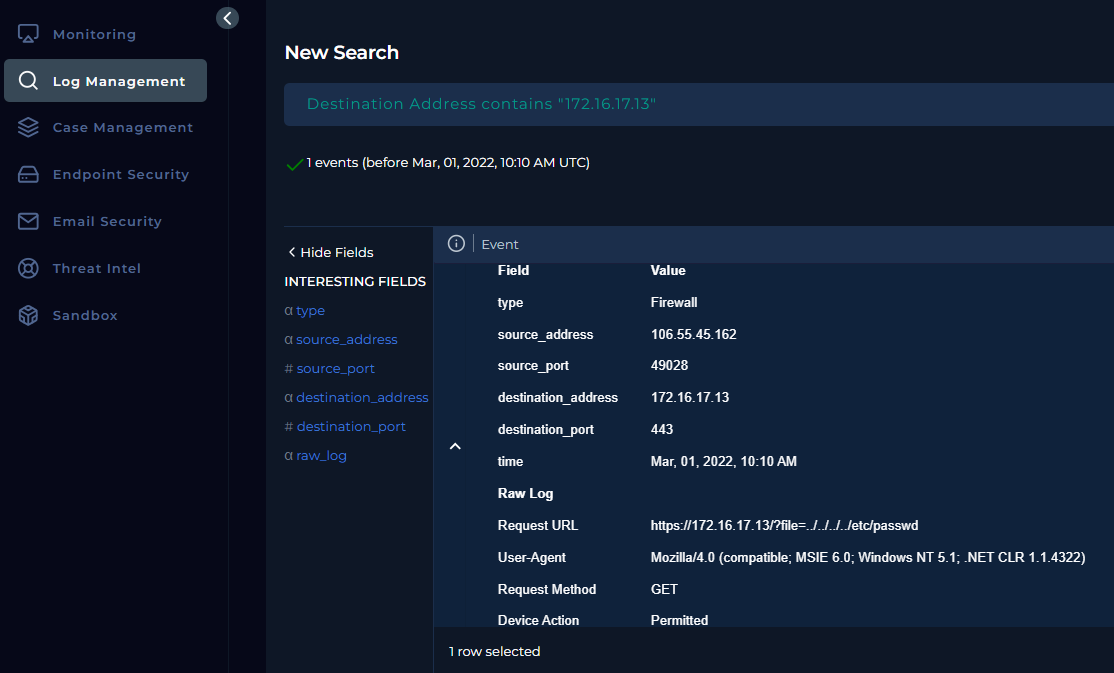
Request URL:
https://172.16.17.13/?file=../../../../etc/passwd -
User-Agent:
Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; .NET CLR 1.1.4322) -
HTTP Method: GET
-
Device Action: Permitted
-
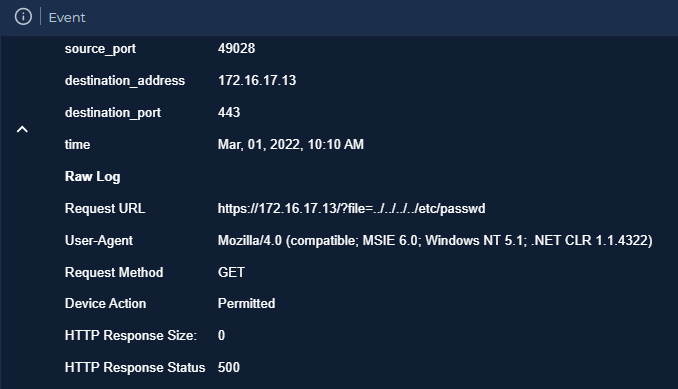
HTTP Response: 500 (0 bytes)
Log Management View
Filtering by destination IP confirms the event:
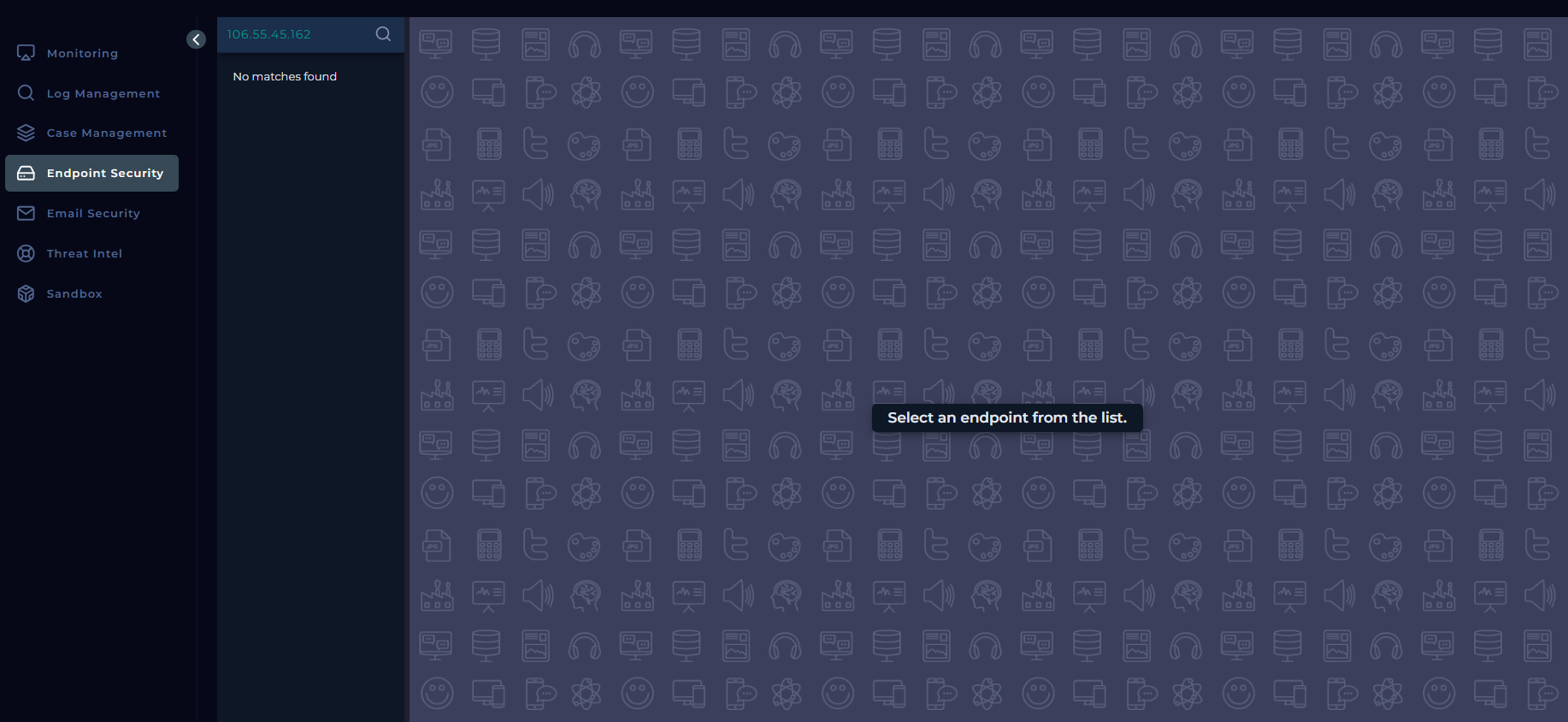
Endpoint Security View
-
No direct endpoint match for the source IP (attacker) was found within the company network.
Analysis Steps
A. Understanding Why the Alert Triggered
-
The rule is designed to catch attempts to access sensitive files like
/etc/passwdthrough directory traversal (LFI) attacks. -
The attacker tried a classic payload by injecting the following into the URL.
../../../../etc/passwd
B. Collect Data
-
Source IP: 106.55.45.162 (Attacker, external)
-
Destination IP: 172.16.17.13 (Web Server, internal)
-
Direction: Internet → Company Network
C. Examine HTTP Traffic
-
The HTTP request was made from the external IP to the internal web server, targeting a sensitive Linux file.
-
Response status was 500 with 0 bytes, suggesting the attack was not successful (the web server likely crashed or timed out rather than serving the file).
Investigation Results
Was the Traffic Malicious?
Yes – The traffic matched the signature of an LFI attack, targeting sensitive files.
Attack Type
-
LFI (Local File Inclusion)
-
The goal was to retrieve sensitive contents from the web server’s file system
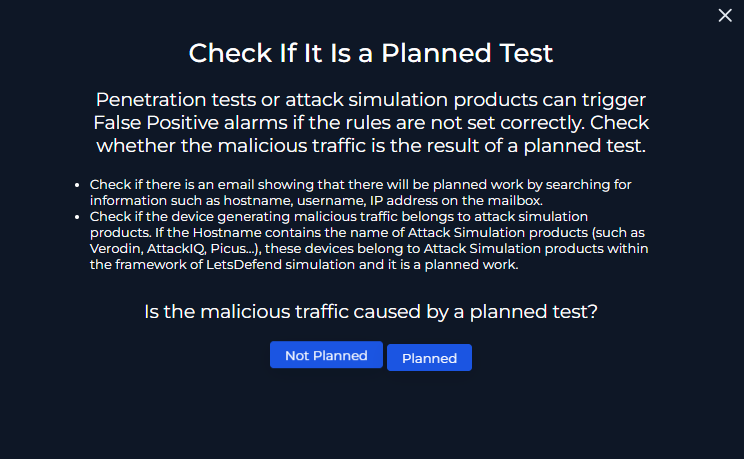
Was This a Planned Test?
- No –there was no evidence of a planned test
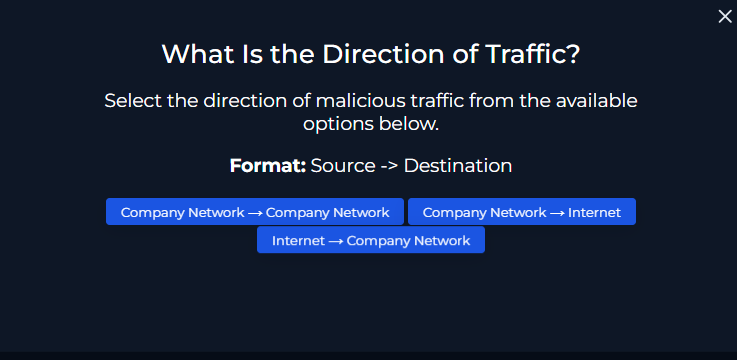
Direction of Traffic
-
Internet → Company Network
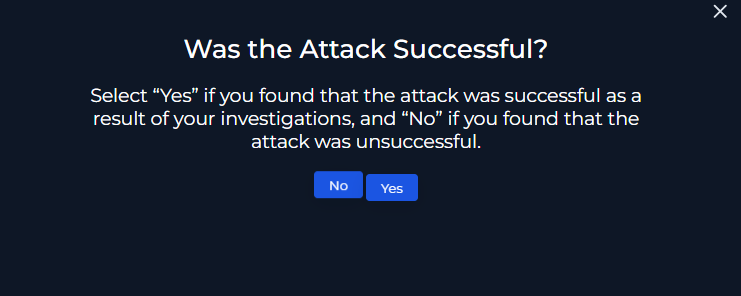
Was the Attack Successful?
No – The web server responded with a 500 status code and did not return any data.
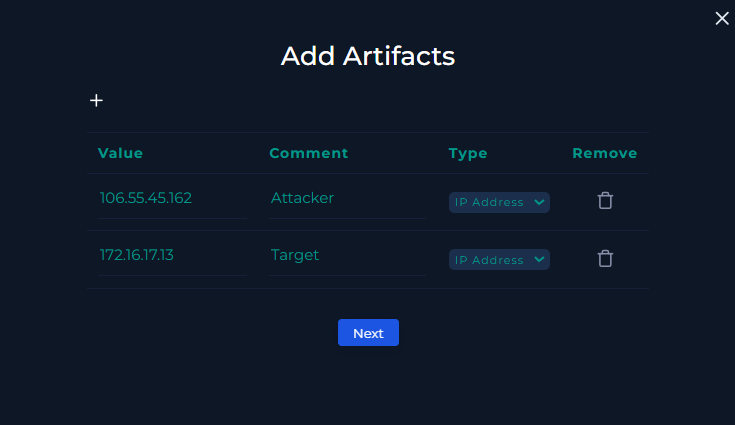
Artifacts
-
Attacker IP: 106.55.45.162
-
Target IP: 172.16.17.13
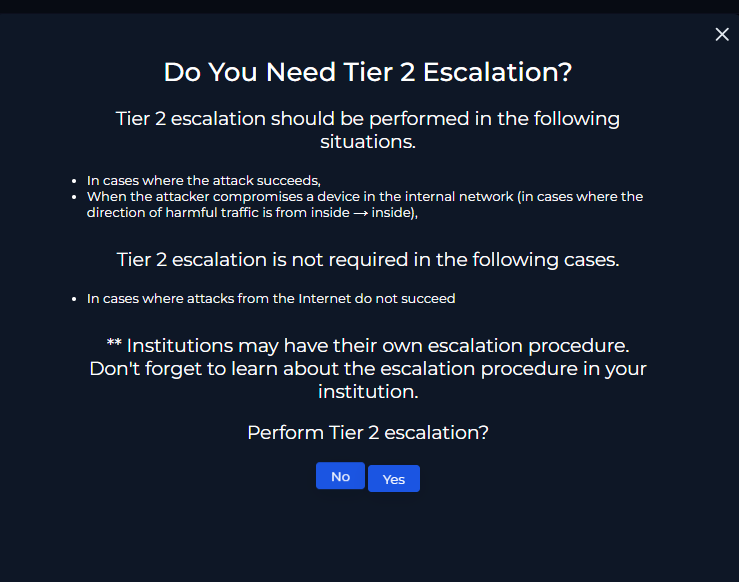
Escalation Decision
Because the attack was unsuccessful (no sensitive data was exfiltrated), Tier 2 escalation was not required.
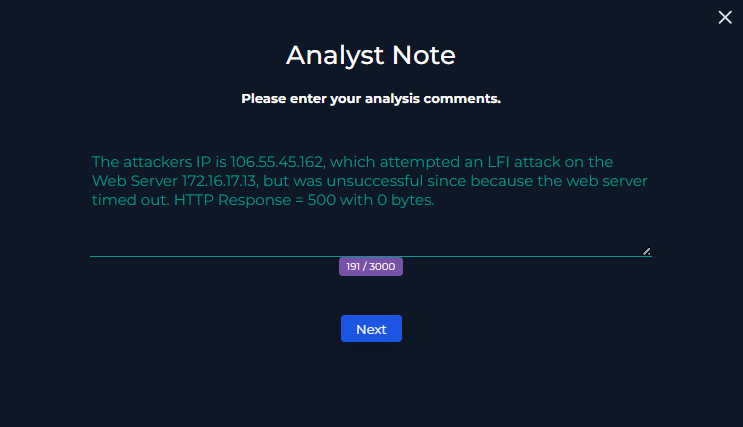
Analyst Note
The attacker’s IP is 106.55.45.162, which attempted an LFI attack on the Web Server 172.16.17.13, but was unsuccessful because the web server timed out. HTTP Response = 500 with 0 bytes.
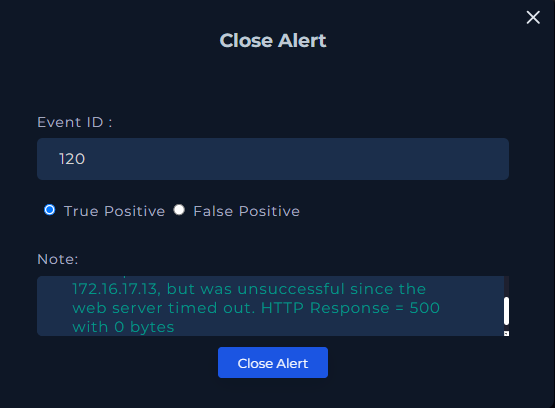
Close Alert
The alert was closed as a True Positive (malicious activity detected), but due to the server’s configuration and timely error response, no harm was done. Escalation was not needed as there was no evidence of compromise.
Lessons Learned
-
Directory traversal and LFI attacks remain common techniques for probing web servers.
-
Even unsuccessful attacks provide valuable information about adversary behavior.
-
Properly handling errors and input validation on web applications is essential to prevent exploitation.