SOC165 – Investigating a Possible SQL Injection Attack
By: Tanner Adler
Introduction
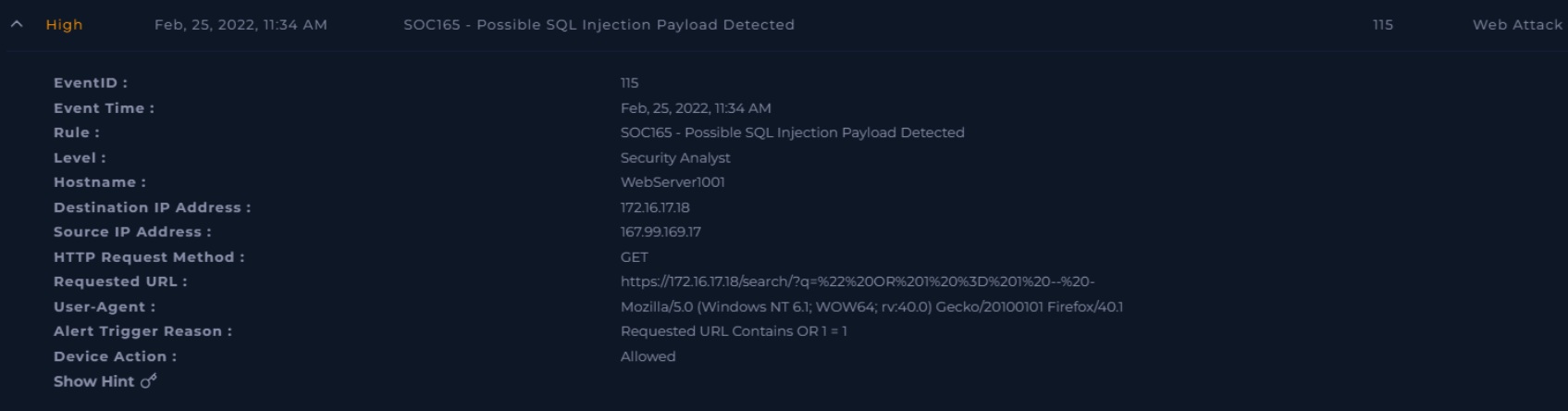
This post walks through my investigation of a “High” severity alert in the LetsDefend SOC platform. The case centers around EventID: 115 (Rule: SOC165 – Possible SQL Injection Payload Detected), which appeared suspicious due to the presence of SQL injection payloads in multiple web requests targeting the company web server.
Alert Overview
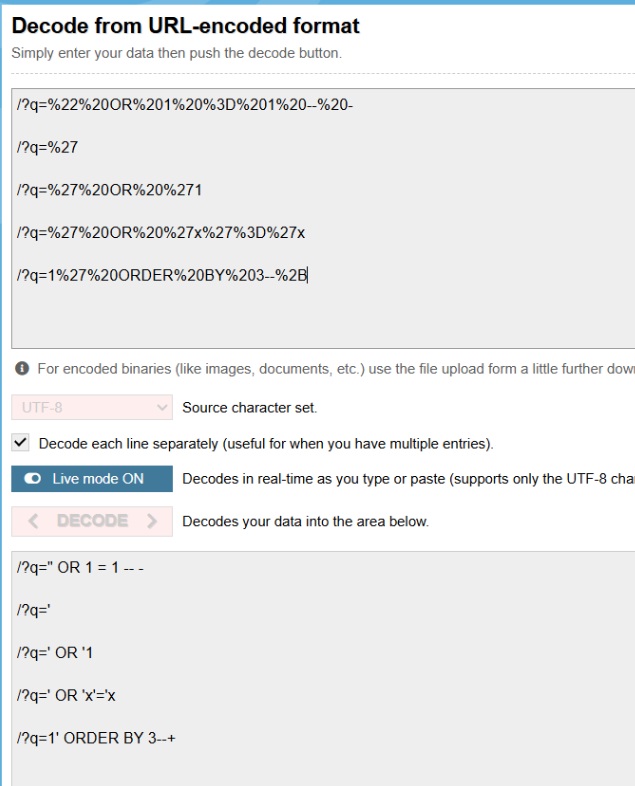
The alert triggered on February 25, 2022, at 11:34 AM, when the SIEM detected SQL injection strings in the requested URL:
This is a classic SQL injection attack, attempting to manipulate the backend query.
EventID: 115
Rule: SOC165 – Possible SQL Injection Payload Detected
Level: Security Analyst
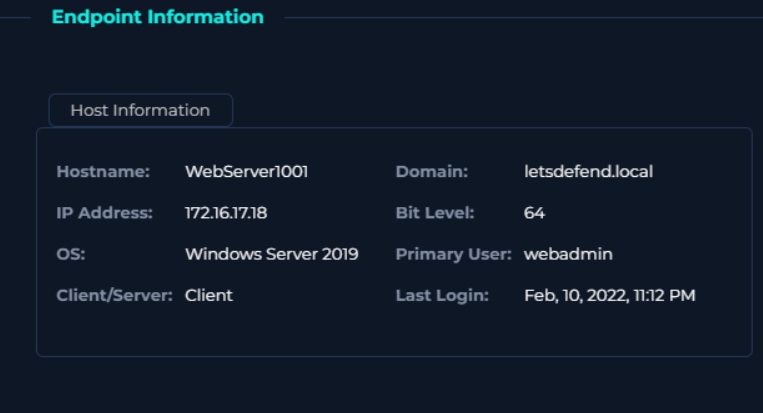
Hostname: WebServer1001
Destination IP Address: 172.16.17.18 (letsdefend.local)
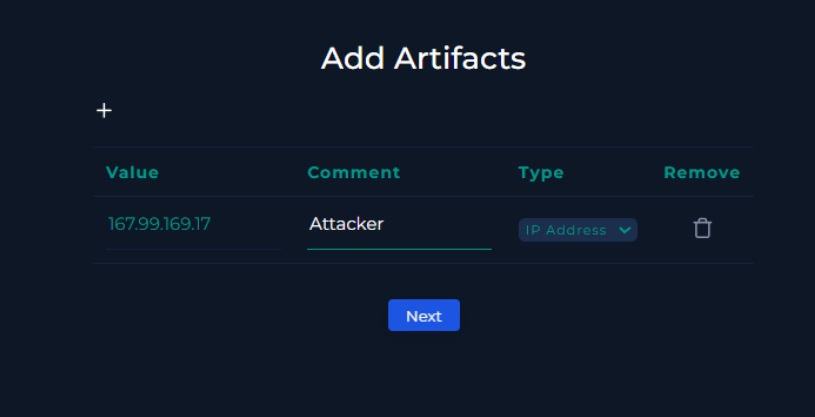
Source IP Address: 167.99.169.17 (Internet)
Request Method: GET
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1
Why Was the Alert Triggered?
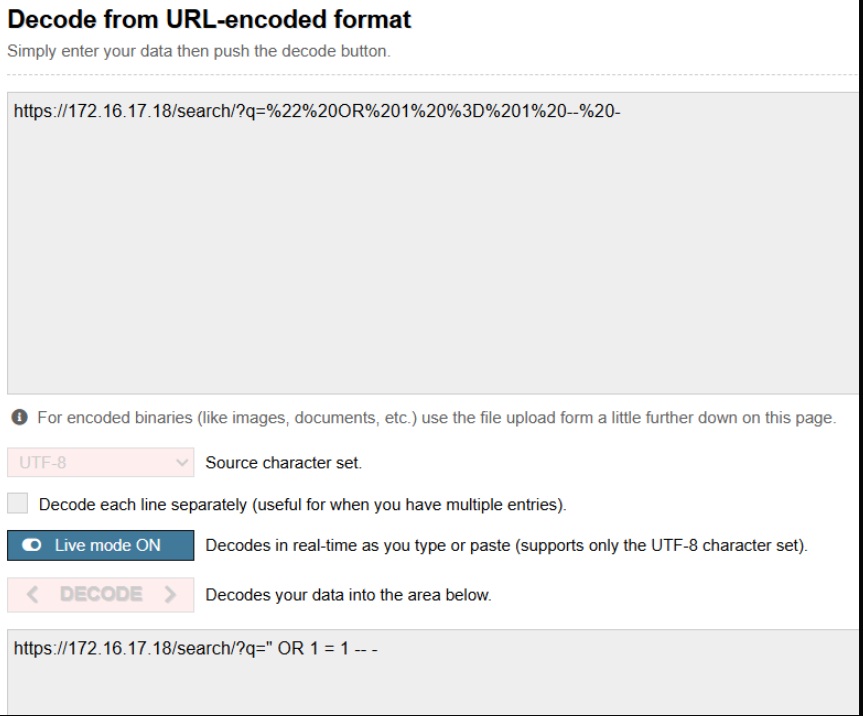
The alert was triggered because it identified a possible SQL injection pattern in a GET request sent to the web server. The request contained a SQL injection test:
This pattern attempts to manipulate database queries by injecting always-true logic.
Collecting Data
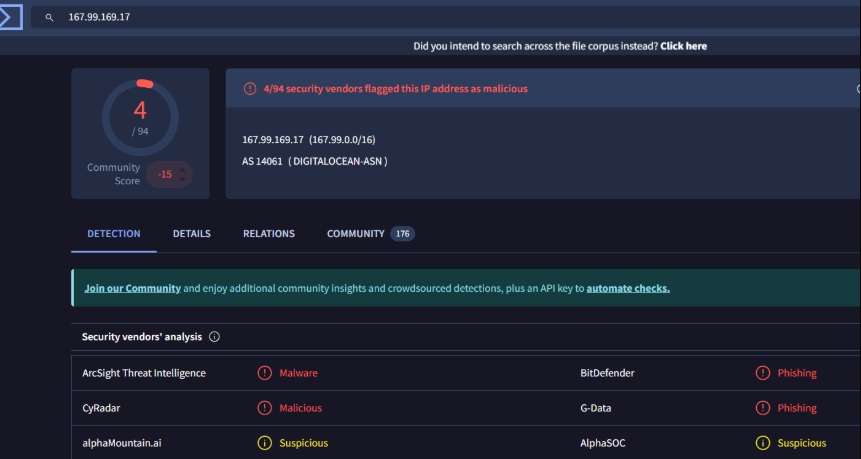
Attacker IP: 167.99.169.17 (confirmed as malicious by VirusTotal)
Target IP: 172.16.17.18 (internal web server, hostname WebServer1001)
Reputation: VirusTotal flagged the attacker IP as associated with malware and phishing.
Examine HTTP Traffic
Below is a detailed breakdown of the raw logs captured during the investigation. These logs show all relevant HTTP requests and responses between the attacker and the web server, confirming the presence of multiple SQL injection payloads.
Log Table
| Source IP | Destination IP | Timestamp | Request URL | HTTP | Resp. Size |
|---|---|---|---|---|---|
| 167.99.169.17 | 172.16.17.18 | Feb 25, 2022, 11:30 AM | / | 200 | 3547 |
| 167.99.169.17 | 172.16.17.18 | Feb 25, 2022, 11:32 AM | /search/?q=%27 | 500 | 948 |
| 167.99.169.17 | 172.16.17.18 | Feb 25, 2022, 11:32 AM | /search/?q=%27%20OR%20%271 | 500 | 948 |
| 167.99.169.17 | 172.16.17.18 | Feb 25, 2022, 11:33 AM | /search/?q=%27%20OR%20%27x%27%3D%27x | 500 | 948 |
| 167.99.169.17 | 172.16.17.18 | Feb 25, 2022, 11:33 AM | /search/?q=1%27%20ORDER%20BY%203–%2B | 500 | 948 |
| 167.99.169.17 | 172.16.17.18 | Feb 25, 2022, 11:34 AM | /search/?q=%22%20OR%201%20%3D%201%20–%20- | 500 | 948 |
The Traffic is Malicious
The request payloads were consistent with SQL injection. This was malicious activity.
Type of Attack
Attack type was confirmed as SQL Injection.
Planned Test
There were no internal communications or emails indicating a planned test. This was not a simulation or pentest.
Traffic Flow
The traffic flows from the Internet to the Company Network.
Was the Attack Successful?
HTTP 500 errors and consistent response size confirm: The attack failed and no data was exfiltrated.
Artifacts & Escalation
Artifacts were added to the case for tracking.
No Tier 2 escalation was needed because no compromise occurred.
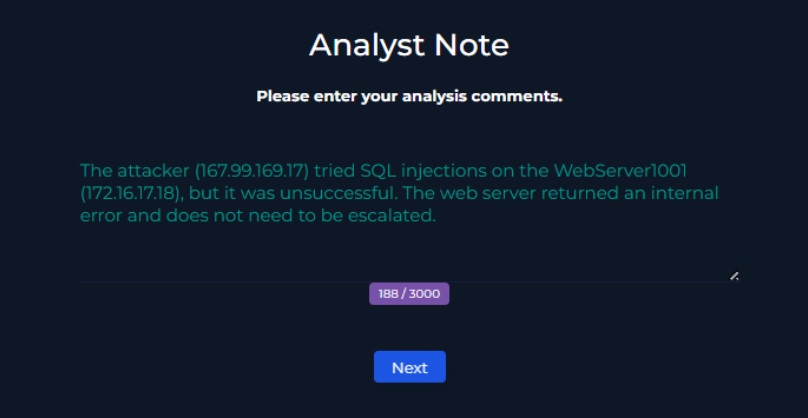
Analyst Note & Closing the Alert
Final notes: The attacker (167.99.169.17) tried SQL injection attacks on WebServer1001 (172.16.17.18), but was unsuccessful. The web server returned internal errors. The incident is recorded as a true positive but required no escalation.
Key Takeaways
Detected a real SQL injection attempt.
URL decoding and log analysis confirmed the attacker’s intent.
Defensive measures prevented a breach.
The incident was fully documented for future reference.